How to implement data security best practices¶
Data is one of the primary targets of attackers. Protecting data is a key consideration for any software design project. The content here builds upon the subject matter found in Engineering Fundamentals and DevSecOps. Be sure to consider the relevant security content there and content presented here.
Microsoft recommends a data security strategy that follows a layered, defense-in-depth approach to protect customer data.
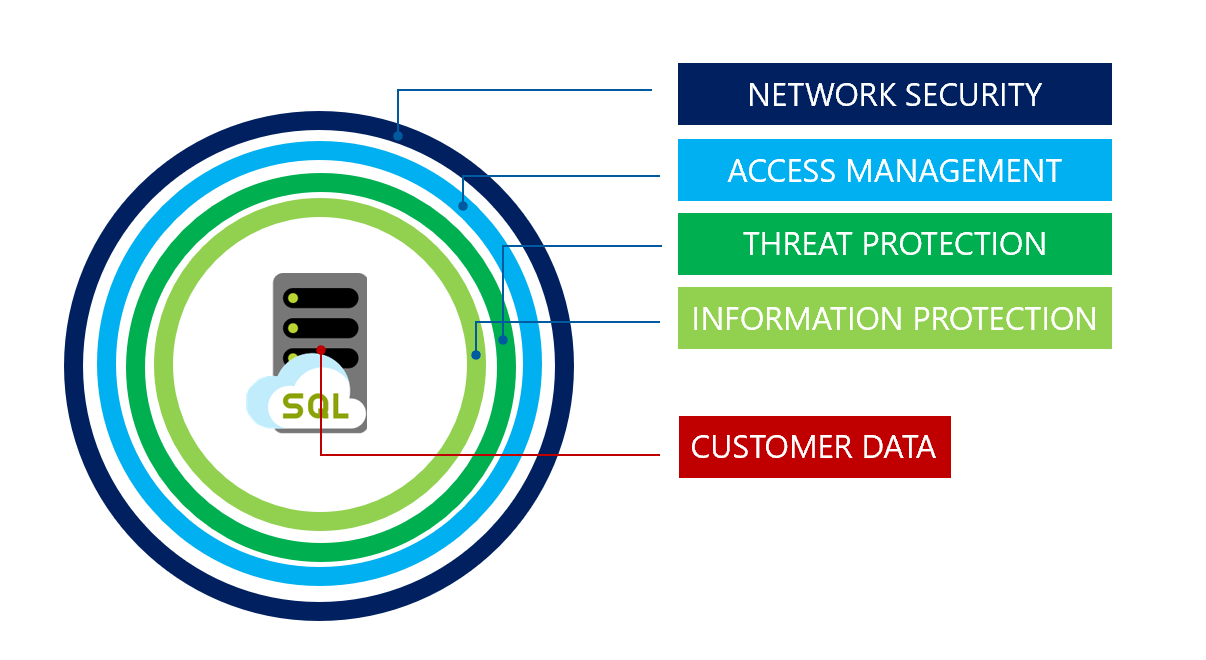
The Microsoft Azure Well-Architected Framework recommends a holistic approach that considers all aspects of the system architecture. Microsoft recommends considering each data service independently to ensure that each service is fully secured. For each Azure data service incorporated in the design, see the recommendations posted in the following linked Microsoft documentation.
Review key takeaways¶
- Ensure the overall architecture implements defense-in-depth practices.
- Every data service in Azure has a set of security recommendations and controls to follow.
- Enabling Azure Defender enables automatic scanning that validates correct implementation of recommended controls.
Perform these actions¶
- Review the Engineering Excellence and DevSecOps playbooks.
- Review The Microsoft Azure Well-Architected Framework to ensure that the entire design follows best principles.
- Review the recommendations for each service incorporated in the design
- Azure SQL
- Azure Blobs
- Azure Files (Be sure to read the related "How-to -> Secure" guides)
- Azure Queues and Azure Security baseline for Azure Storage
- Azure Tables
- Azure Disks
Follow this checklist¶
- Enable Azure Defender for all your storage accounts.
- Turn on soft delete for blob data.
- Use Azure AD to authorize access to blob data.
- Consider the principle of least privilege when you assign permissions to an Azure AD security principal through Azure RBAC.
- Use managed identities to access blob and queue data.
- Use blob versioning or immutable blobs to store business-critical data.
- Restrict default internet access for storage accounts.
- Enable firewall rules.
- Limit network access to specific networks.
- Allow trusted Microsoft services to access the storage account.
- Enable the secure transfer required option on all your storage accounts.
- Limit shared access signature (SAS) tokens to HTTPS connections only.
- Avoid and prevent using Shared Key authorization to access storage accounts.
- Regenerate your account keys periodically.
- Create a revocation plan and have it in place for any SAS that you issue to clients.
- Use near-term expiration times on an impromptu SAS, service SAS, or account SAS.